The latest 2012 HIMSS Analytics Report: Security of Patient Data released in April outlines survey statistics related to data breaches, including preventative measures taken and degree of due diligence with third-party vendors. Commissioned by Kroll Advisory Solutions, the study includes respondents who identify as Chief Security Officers, Senior Information Technology executives, Compliance Officers and Privacy Officers.
The latest 2012 HIMSS Analytics Report: Security of Patient Data released in April outlines survey statistics related to data breaches, including preventative measures taken and degree of due diligence with third-party vendors. Commissioned by Kroll Advisory Solutions, the study includes respondents who identify as Chief Security Officers, Senior Information Technology executives, Compliance Officers and Privacy Officers.
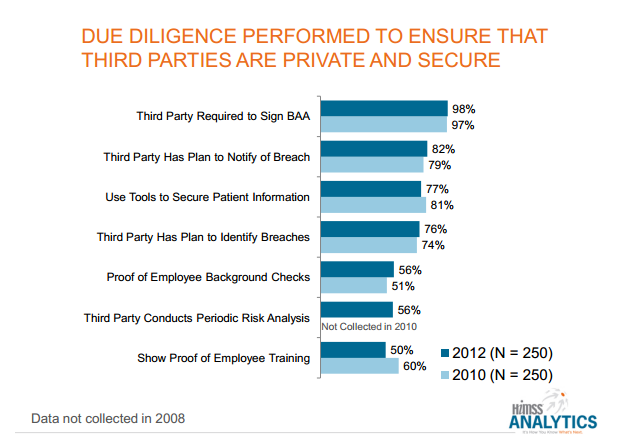
While 98 percent of respondents require third-party vendors to sign a BAA (business associate agreement), only 50 percent require their business associates to show proof of employee training in HIPAA/security policies. The second most commonly practiced method of due diligence is ensuring business associates have a formal breach notification plan in place.
When it comes to breach notification plans, it is essential to have a clause in place that specifically details the timeline by which the business associate will notify the covered entity when a breach is suspected. Online Tech’s breach notification clause states:
2.5. Business Associate shall notify Client in writing of any Breach involving Unsecured PHI within five (5) business days of becoming aware of such Breach. All reports of Breaches of Unsecured PHI shall be made in compliance with HITECH Act § 13402 and the regulations issued thereunder.
A Breach will be treated as discovered as of the first day that such Breach is known or reasonably should have been known by Business Associate. Business Associate shall notify Client within seventy-two (72) hours of any suspected or actual Security Incident or breach of security, intrusion or unauthorized use or disclosure of PHI and/or any actual or suspected use or disclosure of data in violation of any applicable federal or state laws or regulations.
The third most commonly used method is ensuring business associates “use tools to secure patient information.” While the report doesn’t offer any additional details around what “tools” they’re referring to, it may vary from one HIPAA hosting provider to another, as the HIPAA rules do not require any one method of achieving the same security standards.
Seventy-six percent checked to ensure their third-party vendor had a plan to identify breaches, different from the 82 percent that sought out business associates with a breach notification plan. Identifying breaches can be achieved with comprehensive monitoring systems that generate logs of activity on servers, as well as Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS) that can help pinpoint any attempts at unauthorized access to servers that contain ePHI (electronic protected health information).
Checking for proof of employee background checks and periodic risk analyses both ranked at 56 percent in covered entities’ due diligence of business associates. While low on the list, employee background checks are key when it comes to data breach cases.
According to the HIMSS Analytics Report, the most common perpetrators of security breach incidents are employees (79 percent). Although down from 2010’s 94 percent, this still accounts for the majority of PHI breaches within an organization. While this may be attributed to other factors such as lack of employee training, background checks should be implemented regardless for optimal PHI security.
The U.S. Department of Health and Human Services requires covered entities to conduct periodic risk analyses (read What’s in a HIPAA Risk Analysis?). An emphasis on ‘periodic’ is in order, since, like any audit or analysis, a one-time report only measures the security of an organization during a certain snapshot of time. For assurance of ongoing compliance, check their analysis and the scope of their analysis to do your due diligence.
To get educated on what you need to know about third-party vendors to stay compliant, read our E-Tip, Five Questions to Ask Your HIPAA Hosting Provider. Read our other HIPAA-related E-Tips too.