What is Two-Factor Authentication?
The simplest example may be the use of an ATM/debit card – this combines two factors; one is something you own (the card) and the other is something you know (the PIN number).
What is Two-Factor Authentication?
The simplest example may be the use of an ATM/debit card – this combines two factors; one is something you own (the card) and the other is something you know (the PIN number).
Employees and other users may need to log into a private network to access data from a remote location, a VPN (virtual private network). In this scenario, one authentication factor includes logging into a web-based system with a username and password. The second authentication factor may include the use of a cell phone – with a smartphone, you can register your phone number with the system and receive a request to approve.
Or, by using a passcode via text message, you can log into the system with the randomized numbers sent to your phone. You can even answer a phone call and press a key in order to authenticate you are the authorized account holder.
There are other authentication factors that can be used – for example, biometrics requires something specific to you, from a fingerprint to voice recognition. Or, you can use something physical you own, like a keyfob.
Who’s Using Two-Factor Authentication?
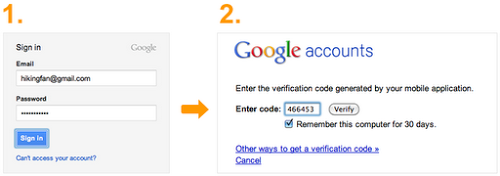
One example of a company using two-factor is Google – they’ve implemented their version called “2-step verification” for Google account holders. After signing into your account with your email address and password, Google requires you to enter a verification code sent to you via text message or generated by your smartphone.

Google’s 2-Step Verification
Any organization concerned about security should consider implementing two-factor authentication for their VPN (virtual private network), regardless of their compliance requirements. Two-factor authentication lowers your risk of a data breach caused by unauthorized remote access to sensitive data.
PCI DSS Compliance Requirements
Two-factor is required by PCI compliance. The Payment Card Industry Data Security Standards (PCI DSS) mandate that organizations who “hold, process, or pass cardholder information” meet a minimum level of security. Part of this security is protecting remote access logins with strong authentication. PCI requirement 8.0 states organizations must assign a unique ID to each person with computer access.
Specifically, section 8.3 requires organizations to implement two-factor authentication for remote access to the network by employees, administrators, and third parties. To achieve compliance with this requirement, you should use technologies such as remote authentication and dial-in service (RADIUS) or terminal access controller access control system (TACACS) with tokens; or other technologies that facilitate two-factor authentication.
Two-Factor Authentication for HIPAA Compliance
Two-factor authentication is also recommended in order to meet HIPAA compliance, as it adds an extra layer of security that can prevent unauthorized access.
A recent article from ModernHealthcare.com demonstrates the need for strong authentication in the healthcare industry. The Privacy and Security Tiger Team of the Health IT Policy Committee is proposing rules for Stage 2 meaningful use that will govern security recommendations to authenticate the identity of patients as they log into their patient portals to download or view their personal health records.
While the policy committee intends to propose a rule requiring at least single-factor authentication while accessing records via a patient portal, two-factor authentication can offer significantly more security with minimal effort and cost.
Related Resources
Read our Two-Factor Authentication for VPN Login FAQ for further information.
Find other PCI compliant resources here. And watch this webinar or read the transcript, PCI Compliance: Detailed Requirements, for a comprehensive overview of the required technology to achieve PCI DSS compliance.
References:
PCI DSS Quick Reference Guide: Understanding the Payment Card Industry Data Security Standard Version 2.0 (PDF)
Defender 5: The Right Way to Prove, Identify and Establish Trust from Quest Software
Federal Privacy Work Group Wants EHRs to Verify Patient ID