A recent article from HealthCareITNews.com details the top five security vulnerabilities that “could mean trouble” – that is, result in a data breach. While these risks are entirely valid, the article doesn’t offer tactical solutions or alternatives to reduce said risks. [Note: these security vulnerabilities should be of concern in any industry, not just healthcare – i.e., financial, ecommerce, software, etc.].
So I thought I would respond:
A recent article from HealthCareITNews.com details the top five security vulnerabilities that “could mean trouble” – that is, result in a data breach. While these risks are entirely valid, the article doesn’t offer tactical solutions or alternatives to reduce said risks. [Note: these security vulnerabilities should be of concern in any industry, not just healthcare – i.e., financial, ecommerce, software, etc.].
So I thought I would respond:
Theft.
The article acknowledges that lost or stolen media, often in the form of a backup tape or laptop, were the culprit for a data breach. The Sutter Health incident involving a break-in and theft of a desktop computer is used as an example. But the article fails to provide a way to prevent the loss of innumerable patient records by media theft.
Keeping ePHI (electronic protected health information) or other sensitive information on secure networks, and not physical devices can greatly decrease the potential risk of allowing thieves access to ePHI. With remote access to networks using mobile devices, the use of two-factor authentication is greatly recommended – it verifies the identity and access level of the user trying reach the data. Read more about this here: Keep ePHI on Secure Networks, Not Mobile Devices, Recommends OCR.
In addition to keeping data in HIPAA compliant data centers with standardized network security in place, investing in an offsite backup solution that doesn’t use tapes can help prevent a data breach.
Mobile devices.
Similar to the theft issue, mobile devices “don’t have the same level of security controls as computer systems,” the article claims. In addition to keeping ePHI/sensitive data off of physical devices, a BYOD (Bring Your Own Device) and mobile policy can standardize users’ behavior when it comes to transmitting, storing and accessing data.
A solid set of policies and procedures, as well as a security awareness and training program can ensure your employees know what is expected when it comes to the use of mobile devices.
Dissemination of data.
Target data sharing between healthcare organizations and third-parties, the article claims the lack of security, tracking and auditing capabilities as a source of data breaches. The article states those that transmit data must “invest in technology and processes that protect the data in transit and at rest.” But what kind of specific technology could do that?
SSL certificates can secure the transit of information from a web server to the user by starting a secure session and encrypting shared data. Encryption for data at rest and in transit should follow the U.S. government, NIST-approved (National Institute of Standards and Technology) AES-256 (Advanced Encryption Standard). Additionally, using SFTP (Secure File Transfer Protocol) to transfer files can help secure and validate the identity of users.
Outsourcing to business associates or third-party vendors.
The article mentions the growth in outsourcing, and the need for business associates, vendors and partners to follow national regulations (HIPAA, PCI, SOX, etc.). The article mentions pre-contract assessments of business associates, and post-contract compliance assessments, but more due diligence should be done pre-contract to minimize as much risk as possible.
Start by asking managed hosting providers for a copy of their Report on Compliance (ROC), for any type of compliance. This means they’ve invested in an independent audit of their facilities and services and were found to be operating at 100% compliance with the standards.
A HIPAA hosting provider should also be able to provide documented policies and procedures of their security practices, dates and signed documentation of employee training, and a comprehensive Business Associate Agreement (BAA) outlining their responsibilities and incident response protocol.
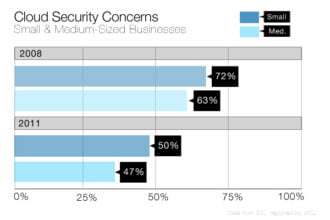
The cloud.
The article gets kind of vague here, stating that cloud computing is popular because it’s cost-efficient to outsource both storage and compliance out to a provider, yet it “adds another layer of potential breach exposure to a healthcare organization.” The article concludes by stating the responsibility of securing information in the cloud is ultimately on the shoulders of a covered entity, which is true, but can be alleviated by doing their due diligence as described above.
Another article I wrote, Outsourcing Cloud Computing Security, outlines sample questions to ask your potential new HIPAA cloud hosting provider. Cloud Computing and Compliance also explains the difference between Software/Infrastructure-as-a-Service.
Healthcare Organizations: Seeking a Cloud Provider? BAAs Required quotes David S. Holtzman of the HIPAA enforcement entity, OCR (Office of Civil Rights):
If you use a cloud service, it should be your business associate. If they refuse to sign a business associate agreement, don’t use the cloud service.
The article also lists important provisions in your cloud contract to minimize security vulnerabilities and ultimately protect your PHI.
References
5 Security Vulnerabilities That Could Mean Trouble