The Health Insurance Portability and Accountability Act (HIPAA) has many physicians nervous about their responsibilities in protecting patient information. Respecting patient privacy has always been both a moral and legal issue, but new technologies raise new questions about how to safeguard confidential information.
The Health Insurance Portability and Accountability Act (HIPAA) has many physicians nervous about their responsibilities in protecting patient information. Respecting patient privacy has always been both a moral and legal issue, but new technologies raise new questions about how to safeguard confidential information.
 Electronic protected health information (EPHI) refers to individually identifiable health information that is created or stored electronically. Like a traditional chart, strict rules govern who can access EPHI.
Electronic protected health information (EPHI) refers to individually identifiable health information that is created or stored electronically. Like a traditional chart, strict rules govern who can access EPHI.
In my next post, I’ll tell you about specific ways to control access to patient health information. Today, I’ll focus on the broader issue of data security.
HIPAA requires healthcare providers to assess their data security risks and take reasonable measures to safeguard patient information. Choosing the right electronic medical record (EMR) software is essential to keeping data secure and complying with HIPAA guidelines.
EPHI Encryption
Encryption is a method of encoding data that allows only authorized readers to properly view it. Encryption makes data indecipherable—or cryptic—to unauthorized eyes. Intended audiences, such as physicians and administrators, are able to view data when they possess a key. Effective keys can be as simple as username-password combinations and as complex as biometric recognition of fingerprints or retinas.
While EPHI encryption is not yet required by law, the Department of Health and Human Services recommends encryption as a best practice for protecting patient information. The best EMR softwares encrypt this data at all times—in transmission and at rest.

Most internet users are familiar with little lock icons near the address bar. These icons tell you when your transmissions are encrypted.
However, many users don’t realize that data at rest on their hard drive may not be encrypted. It is important to encrypt data at rest to protect confidential information in the event of loss or theft.
Theft and loss of unencrypted hard drives and portable devices account for the majority of HIPAA breaches.
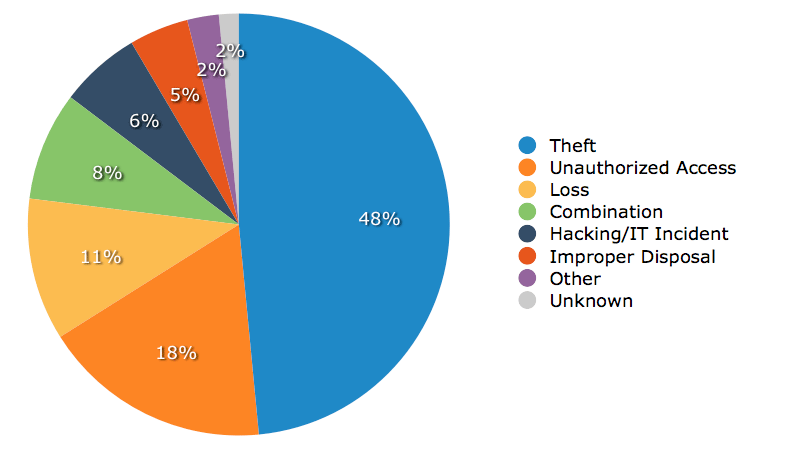 Source: The Proftiable Practice
Source: The Proftiable Practice
The risks of theft and loss can be further mitigated by storing data on dedicated off-site servers—in the cloud.
What About Cloud Solutions?
Cloud-based solutions are not inherently more or less secure than on-premise solutions. It’s all about how the system is set up and the software it uses.
While running an EMR on a cloud provider may seem more vulnerable, the crucial factor is the security measures put in place by the provider. The same is true for on-premise solutions—nearly all of which also have exposure to attacks from the internet. Cloud-based solutions are often more secure because they are managed by expert teams—something that smaller organizations may not be able to afford on-premise.
What is clear is that cloud solutions for healthcare providers must provide access controls and encryption to prevent security breaches. The best cloud networks use encrypted storage, not only for active data, but also for backups.
Cloud solutions decrease the burden on hospital IT departments and save smaller clinics the costs associated with building and maintaining expert security systems. Choosing the right cloud provider is one strategy to simplify the complexity of meeting HIPAA standards.






